
T-DAR T-1000/2000
M/T
MantrapTailgate Prevention System
The T-DAR mantrap system affords the highest levels of security by actually preventing the act of tailgating or piggybacking through a protected portal. This is accomplished by adding a second door and accompanying walls to the existing security entrance portal (see figures below), and then equipping the newly created vestibule with a T-DAR mantrap system. This system operates as fast as a person can open and close the doors and the access control credential can be processed.
There are a few constraints regarding mantrap installation,
as follows:
• Ceiling height must be greater than 8 foot
• Each camera head protects an area roughly 5 ft. by 5 ft., therefore
the space to be protected should be designed accordingly. An example would
be that a T-2000 M/T can protect an area roughly 5 ft. by 10 ft.
• Inward swinging doors on the public side of the vestibule will
require the installation of an inward swinging door sensor available from
Newton.
The following images show an overhead view of an existing portal where there are no provisions for the prevention of tailgating into the protected area, followed by the modifications to this same portal for tailgate prevention using T-DAR. Image 1 shows a standard configuration where a standard pedestrian door has been equipped with standard access control equipment as follows: Card Readers (CK) for access as well as egress, Door Position Switch (DPS) for door status monitoring, and an Electronic Lock (LK) for securing the door. The public and secure areas are noted also.
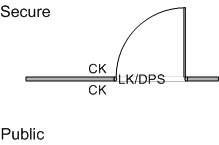
Image 1
Image 2 depicts the addition of walls and a door on the public side of the door to create a vestibule. It should be noted that this same modification could be made on the secure side of the door as well, depending upon available space. In addition to the walls and doors, note the addition of the electronic lock and the door position switch on the new door. The new door is named Public and the existing door is named Secure. It is recommended that doors equipped with sight glass be used so that persons desiring access and egress can verify the status of the vestibule and not be confused by encountering locked doors.
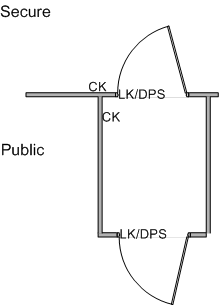
Image 2
Image 3 depicts the newly completed space with the T-DAR components installed in the correct location to allow optimal performance. This particular configuration of the T-DAR stereo camera heads allows for the performance of active scanning of the protected area to ensure that all unauthorized and suspicious transactions are detected. Additionally, the location of the event camera allows the documenting of the violation and provides a loop of quality head-to-toe video information for immediate review.
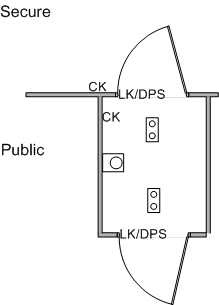
Image 3
The T-DAR system is a high technology solution to the age old question
of how to ensure that only authorized persons go through protected doors.
While today’s access control systems and biometric devices do a
very good job of ensuring that only authorized users can open a door,
they still cannot prevent those users from letting others in behind them
whether accidentally or intentionally. T-DAR is Newton Security’s
solution for giving access control back to the security manager.